As per the report given by Gartner, by 2022 the worldwide information security market is forecasted to reach $170.4 billion. Due to human error, 95% of cybersecurity breaches are caused and these cyber incidents can have massive ramifications. The 21st century global and online media is not without bright ideas and at the same time not without notorious hackers. Data breaches and cyber-attacks can take down the framework of a website or webpage in a couple of hours and you won’t even see them coming. What can keep the situation in control or rather, prevent it from imploding is an Incident Response Plan.
An incident response plan is a documented, demonstrated and well-written plan with 6 distinct phases that helps IT professionals and staff locate, identify and deal with occurrences of a cyber breach.

Is an Incident Response Plan a stipulated requirement of PCI DSS?
Indeed, it is. Requirement 12 of the PCI DSS states clearly and without fail, the steps businesses must take with regards to their incident response plan. The points mentioned by PCI DSS:
- 12.10.2 – Test your incident response plan at least once every year
- 12.10.3 – Give certain employees the responsibility to be available 24/7 to deal with cyber breach incidents
- 12.10.4 – Properly and regularly train the staff with incident response responsibilities
- 12.10.5 – Set up tropes and alert systems for intrusion-detection, intrusion-prevention, and file-integrity monitoring systems
- 12.10.6 – Implement an algorithm to periodically update and manage the incident response plan per industry and organizational changes
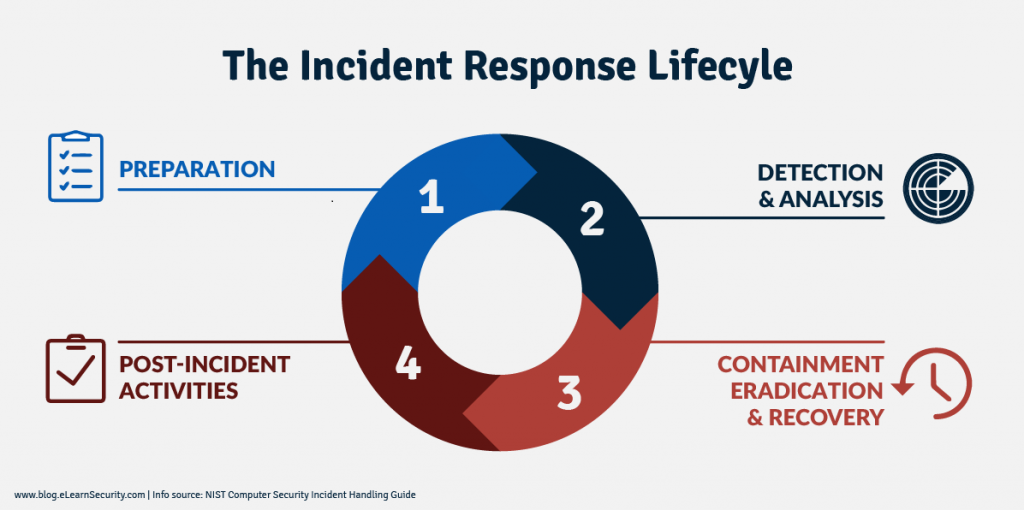
Source: https://cyberhoot.com/wp-content/uploads/2020/01/IR-Lifecycle-by-NIST-eLearnSecurity.png
How to curate the most efficient Incident Response Plan?
An Incident Response Plan should be tailored keeping in mind the cyber breach and the operation of elimination of the cyber breach is carried through several phases of the plan. Every phase will address the issue and deal with a certain aspect of it. The duty of impeding cybersecurity infringement is distributed between these different phases.
The incident response phases are:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Retrospection
We need to dive into the details of each phase to know how they come together to forge a potent Incident Response Plan.

1) Preparation
This is the foundation of your incident response plan. The entire framework will be entwined with the preparation that goes it sketching a blueprint. In the end, this will be the engine your online security system runs on.
For immaculate and well-coordinated preparation, you need to ensure that the employees under you are qualified enough. They should have the experience to react right in situations as jeopardizing as a cyber breach. Try and develop incident response drills, scenarios, and mock data breaches to grade your incident response plan. This will also help you in the evaluation and management of your team.
The different segments of your incident response plan should all be well funded and employees well-trained.
An incident response plan has to be well documented, thoroughly explaining the roles and responsibilities of the entire team. The plan must be then given dry runs so as to assure that your employees will execute their responsibilities as they’ve been trained.
The more prepared your employees are, the less likely they are to make mistakes.
Questions to be addressed:
- Have all participants of the response team been well versed with their roles and responsibilities?
- Was the incident response plan approved by appropriate management and security checks?
- Did you evaluate all Incident Response Team members during the mock drills?
- Has everyone been trained on security policies?
- Is your team aware of the importance of incident response plans? And how instrumental they are in tackling security breaches?
2) Identification
This is the segment of Response Plan creation where you determine a security breach. Has a crack been created in your framework and is being navigated by a hacker? A breach, or incident, could occur in different areas.
Questions to be addressed:
- When did the event happen?
- Where did it happen?
- Who discovered it?
- How was it discovered?
- Have any other areas been afflicted with its impinging influence?
- What is the scope of the compromise?
- Has the point of entry of the external virus been discovered?
- Does it affect the operative components of the website?
3) Containment
When a breach is first discovered, the course of action you should follow is the deletion of all data. This will contain the breach within the confines of the website. The deletion of valuable data is likely to affect you in the long run but it’s all about creating a better incident response plan to prevent it from happening again.
Containment of breach prevents the venturing of a breach into other areas of your network so as to restrain it from causing any further disaster. If you can, disconnect all the affected devices from the network frame.
Keep in-store, a short-term as well as a long-term containment strategy. One is for immediate reaction and the other is for rebuilding. A redundant system back-up can also come in handy to help you in restoring the business operations. Follow the above and most of the data will be preserved and even retrieved if lost in certain cases.
Questions to be addressed:
- What’s been done to contain the breach short term?
- Does your remote access require true multi-factor authentication?
- Has any discovered malware been isolated from the rest of the network?
- What all backups are in place to tackle any future breach?
- Have all access credentials been reviewed for legitimacy, hardened and changed?
- Have you patched the fault and made all updates?
- What’s been done to contain a long term breach?
4) Eradication
Once the issue has been contained within the boundaries of the website it’s time to eradicate it. All malware should be removed, passwords ought to be hardened and the system framework has to be patched back into its original shape. Find the root causes of the breach before you enter this stage of the incident response plan.
You can do this yourself or hire a third party to do it for you. Either way, be careful that the phase is executed right. Any lapses in removal of malware are likely to hurt you in the long run. You also run the risk of losing valuable data in such a situation.
Questions to be addressed:
- Has all malware from the hacker been isolated and safely removed with due action?
- Has the system been hardened, patches and updates applied?
5) Recovery
During the recovery phase, all affected systems and removed devices are restored to absolute normality. You need no longer fear the breach. Your sole aim should be returning things, back to their initial state.
Questions to be addressed:
- When can systems be turned back to production?
- Has the system been hardened, patched, and updated?
- Can the deleted information and lost data be retrieved from a trustworthy back-up?
- How long is there a need to monitor the patched network and assess it for restored efficiency?
- What tools will you need to add to your arsenal to prevent the occurrence of another breach?
6) Retrospection
Once the first five steps have been applied and executed it’s time to look back but not in anger. Hold an after-action meeting with all Incident Response Team members and make a note of everything. The area of the breach, the responses, the extent of the breach, and failures that allowed the spread of the breach. It is responsible behavior to analyze and document every aspect and ramification of the breach. Identify what part of the Incident Response Plan proved to be the savior and what part of the system was culpable in the overall inability to prevent the cyber-attack.
Questions to be addressed:
- What additions need to be made to the security system?
- Should any of the employees be subjected to another kind of training? If yes, then of what kind?
- What weakness did the cyber breach exploit?
- How will you ensure a similar breach doesn’t happen again?
Just like any experience in life, security breaches give you a lot to learn. Make sure you don’t make the same mistakes again and are readily prepared to defend yourself from another future cyber-attack.
Here are some books and sources to dive into to prepare the most efficient Response Plan:
- Code Reviews: A Method to Reveal Costly Mistakes
- The Beginner’s Guide to Combat Phishing
- Security Patches in Your Business: Complying with PCI Requirement 6.1
There are times and situations in which you’ll find your website in a precarious position due to cybersecurity breaches and hacks. In such a situation you need a Six-Step Incident Response Plan as talked about to pull yourself through. Your website is your intellectual property. Do all you can to preserve and guard it against the malicious contents streaming through the web?




I really like the way you write blogs
Most people wrongly believe that an incident plan means that an organization needs to take few steps which need to be performed when an incident happens. Not true. The incident response needs to be 24/7. This helps in immediate response and can prevent damage.
Glad to see such a comprehensive and well-researched post!
Cybercrime will be the no 1 crime in the coming years. Thanks, Katie especially for the prevention tips. We really need these kinds of articles.